Learn from experts. 10 OSINT blogs you should follow.
Open-Source Intelligence blogs that will help to improve your skills. A curated list of topics from cybersecurity, threat intelligence to GEOINT.

Whether you are just starting to learn OSINT or are already a seasoned expert, staying connected with the community can always help you grow. Blogs serve as one of the best sources for learning, especially when authors put in sufficient effort. Writing blogs on your own can is time-consuming. To acknowledge the hard work, I've selected ten personal blogs, provided background information on the authors, and shared a favorite article from each. Below is a list of hand-picked OSINT blogs along with their authors' Twitter handles:
- Webbreacher.com by Micah Hoffman
- Dutchosintguy.com by Nico Dekens
- Raebaker.net by Rae Baker
- Osintme.com by Maciej Makowski
- Offensiveosint.io by Wojciech
- Nixintel.info by Steven Harris
- Hatless1der.com by Griffin Glynn
- Gralhix.com by Sofia Santos
- Krebsonsecurity.com by Brian Krebs
- Blog.bushidotoken.net by Will Thomas
Micah Hoffman
Webbreacher.com is the personal blog of Micah Hoffman. I don't even know where to begin describing his persona. Firstly, he is a founder of My OSINT Training, a platform offering a wide range of courses. Secondly, he is a co-creator of osint.games and a SANS course instructor. The rest is for you to discover on his website.
Favourite article

Initially, I thought my favorite article would be about the Obsidian documentation tool. I first heard about Obsidian from Micah back in 2019 but only recently decided to try it. Well, I wish I had tried it sooner. However, I came across an article on analytical methodology later, and it surpassed the Obsidian article for me. I find "Analytical Methodology" more valuable, as the brain is your most important OSINT tool. Although the article is focused on intelligence, you can apply the described methodology in various research cases. Biases and false conclusions are tendencies present in every analysis, so I highly recommend learning analytical methods.
Nico Dekens
Dutchosintguy.com is the personal blog of Nico Dekens. He is an All Source Analyst with expertise in Open Source Intelligence (OSINT), online Human Intelligence (HUMINT) and online investigations. Additionally, he is a SANS Institute instructor for the Practical Open-Source Intelligence and Advanced Open-Source Intelligence Gathering & Analysis courses.
Favourite article

Is the second article about analytical thinking? Indeed, it is. Tools are only as useful as your understanding of how to use them. In the article, Nico describes questions to ask when creating an intelligence report. He stresses that question you couldn’t answer are as important as the one you could. On top of that, Nico shares his workflow for conducting OSINT research. I'm certainly taking a page from his book!
Rae Baker
Raebaker.net is the personal blog of Rae Baker. She is the foremost expert in Maritime Intelligence, focused on hunting vessels and tracking elusive AIS signals. As a Senior OSINT Analyst in Adversary Intelligence, she specialises in Human Targeting and Corporate Reconnaissance. In addition, she is a co-founder of Kase Scenarios, a training ground where you get hand-on investigative experience solving immersive cases.
Favourite article

The article stresses, that your OPSEC is as good as your sock puppet, so make a solid one. AI is not just a buzzword being thrown in the article, it really helps to create more believable sock puppet. Rae covers utilising ChatGPT to develop lifelike personas and discusses the usefulness of Generative AI in creating fake images. In conclusion, this guide is essential reading for anyone interested in staying up-to-date with technological advancements.
Sofia Santos
Gralhix.com is the personal blog of Sofia Santos. She is a senior OSINT analyst at the Centre for Information Resilience. Probably, she is the first person who comes to my mind when talking about geolocation challenges. She stays active on social media and posts lots of OSINT exercises. If you are curious what it takes to consistently post challenges, she nicely sums it in the round-up post.
Favourite article

Sofia demonstrated remarkable skill in quickly geolocating a video that might appear impossible to the average person. I like how she went out of the box and checked traffic jams on the road, which would be a result of the damage made by excavators. This clever shortcut saved significant time that would otherwise have been spent geolocating visual clues. Even if you're pressed for time and can't read the full article, it's worth noting this smart approach
Maciej Makowski
Osintme.com is the personal blog of Maciej Makowski. He served in Garda's Security & Intelligence Section and worked with International Police Association. Later on he transitioned into the private sector and began working in information security.
Favourite article

Diagrams, diagrams, and more diagrams - I can't get enough of them! I love them as much as any visual representation of the data. They help to convey topics of any complexity. While the article covers OSINT from defensive perspective, it certainly improves your offensive skills as well. I like how the article is divided in sections, where each one is responsible for a particular investigation flow. It's a must-read for anyone looking to sharpen their profiling skills.
Wojciech
Offensiveosint.io – is the personal blog of Wojciech, seasoned Systems Engineer, Pentester, Security Analyst and OSINT researcher. Throughout his career he has developed many OSINT tools, including Kamerka, LeakLooker-X and Danger Zone. Kamerka gained significant recognition, being featured on platforms like Vice and ZDNet. Building on the success of his OSINT tools, Wojciech created an even more advanced tool called Open Source Surveillance. This tool facilitates the investigation of social media, testing the security of devices, searching for insecure networks, and tracking cameras in real-time.
Favourite article

What could be more fun than debunking internet scams? This article delves into a variety of clearnet frauds, offering valuable insights. It's divided into two parts, and I highly recommend going through both. While you need to subscribe to access the articles, it's definitely worth it. In the first part, the author explains how to research websites, utilize web scraping, and use Maltego to piece everything together. The second part completes the story by demonstrating how to investigate phone numbers and connect suspects.
Steven Harris
Nixintel.info is the personal blog of Nixintel, a highly experienced investigator and cybersecurity specialist. Steven specialises in Open Source Intelligence (OSINT) and has more than 15 years’ experience of conducting internet investigations. Currently he work as a Cyber Threat Analyst at Protection Group International. Like many well-established Intelligence Analysts, he has authored a SANS course (SEC497 Practical Open Source Intelligence).
Favourite article

Steven demonstrates the power of the Command Line Interface (CLI) in streamlining the intelligence collection process. He delves into uncovering the IP address of websites hidden behind Cloudflare. Notably, there are a lot of domains protected by Cloudflare, so mastering this technique will definitely help you in the future. Through his investigation, Steven not only identifies the hosting company but also provides pictures from their data center, solidifying his findings through meticulous verification.
Griffin Glynn
hatless1der.com is the personal blog of Griffin. He has spent nearly 20 years working investigations in the private sector alongside all levels of law enforcement; learning, leveraging, and teaching open source intelligence techniques throughout that time. Griffin Glynn is a Chief Investigations Officer for the National Child Protection Task Force. In addition, he is a co-creator of osint.games, along with above mentioned Micah Hoffman.
Favourite article

Fraud investigation articles with a good sense of humor are always enjoyable to read. Griffin demonstrates some clever techniques to de-anonymize scammers, mixed with the keen humor of an OSINT researcher. Long story short, he uses social engineering to uncover the identity of the scammer. Reading the article taught me some Social Media Intelligence (SOCMINT) tricks, making it useful for me. The article was also discussed in detail on the Cloak and Dagger podcast.
Brian Krebs
Krebsonsecurity.com is the personal blog of Brian Krebs. Brian Krebs is well-known cybersecurity researcher who worked as a reporter for The Washington Post from 1995 to 2009. He is also a top-ranked global speaker and participated in may cybersecurity events. His blog is heavily focused on cybersecurity and threat intelligence. I appreciate the originality and in-depth approach he uses to write articles.
Favourite article
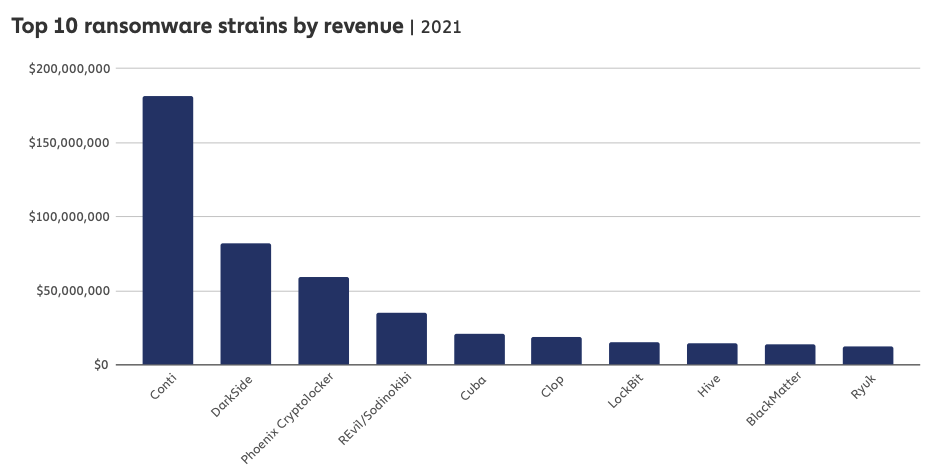
Read this article to delve deep into Threat Intelligence. The most interesting part for me was how Conti hackers used OSINT to gather information on their targets. The hackers were monitoring victims' financial activity using Crunchbase Pro and Zoominfo subscriptions. They also secretly bought a CobaltStrike licence, which served as groundwork for the installation of ransomware on a victim network. It is worth reading how their vast criminal network was operating using publicly available information.
Will Thomas
blog.bushidotoken.net is the personal blog of Will. He is a Threat Intelligence Researcher at Equinix, one of the leading digital infrastructure providers. Additionally, Will is an award-winning CTF participant and is a co-author @SANSForensics.

Stylometry is a technique frequently used to determine the authorship of anonymous documents. It employs statistical methods to analyse style in order to determine authorship. While stylometry traditionally applies to written language, it can also be utilised for analysing code and ransom notes. Will Thomas used this technique to determine if new ransomware families were linked to established threat actors. He conducted a thorough research and concluded the article with a definitive answer.
Conclusion
I hope you enjoyed the list and found these blogs useful. This is not an exhaustive list of authors, and in the future, I plan to review more blogs. Open Source Intelligence is used in many domains, so I aimed to select a diverse set of authors. Reading about OSINT from different perspectives is valuable for personal growth. What is even more valuable is content writing. Start your own blog and contribute to the community. By the way, I recently posted a guide that will help you to go from zero to self-hosted blog in no time. Good luck on your journey!








